Online security is a paramount concern in today’s digital world. With the increasing threats of cyber attacks and data breaches, it is crucial for individuals and organizations alike to protect themselves against potential risks. This is where Cyber Essentials comes into play. Cyber Essentials acts as a safeguard, providing a comprehensive guide to ensure online security. By implementing the Cyber Essentials framework, businesses and individuals can fortify their defenses, mitigate risks, and keep their sensitive information safe from cyber threats. In this article, we will delve into the world of Cyber Essentials, exploring its importance, key features, and the necessary steps to unlock a strong online security posture. Let’s embark on this journey to discover how Cyber Essentials can empower you to navigate the digital landscape confidently.
Understanding Cyber Essentials
Cyber Essentials is a comprehensive framework that aims to enhance online security and protect organizations from cyber threats. It provides a set of fundamental security measures that businesses can implement to safeguard their digital assets and mitigate the risk of cyber attacks. By adhering to the Cyber Essentials guidelines, companies can establish a strong foundation for their online security practices.
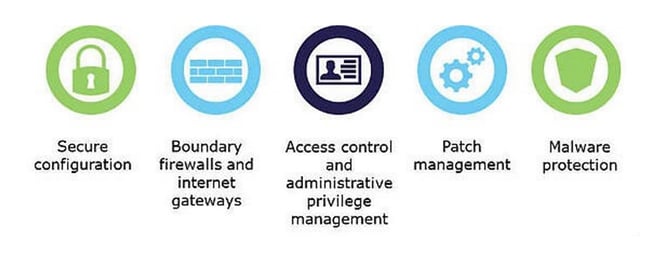
The Cyber Essentials framework focuses on five key areas: boundary firewalls and internet gateways, secure configuration, user access control, malware protection, and patch management. These areas are crucial in preventing unauthorized access, securing network infrastructure, managing user privileges, and ensuring that systems are up-to-date with the latest security patches. By addressing these aspects, organizations can significantly reduce their vulnerability to common cyber threats.
Implementing Cyber Essentials not only helps organizations protect their own information but also builds trust and confidence with their customers and partners. By showcasing a commitment to cybersecurity best practices, businesses can demonstrate that they take the protection of sensitive data seriously. This can lead to improved business opportunities and partnerships, as more stakeholders recognize the importance of working with security-conscious organizations.
In today’s interconnected digital landscape, cyber threats are constantly evolving and becoming more sophisticated. Cyber Essentials provides a proactive approach to online security, enabling organizations to stay ahead of potential risks and ensure the integrity and confidentiality of their systems and data. By understanding and implementing the Cyber Essentials framework, businesses can safeguard their digital environment and establish a solid cybersecurity posture. Stay tuned for the next section, where we will explore the benefits of adopting Cyber Essentials in more detail.
Key Components of Cyber Essentials
Vulnerability Management:
One of the key components of Cyber Essentials is effective vulnerability management. This involves identifying and addressing any weaknesses or vulnerabilities within an organization’s systems and networks. By regularly scanning for vulnerabilities and promptly patching or fixing any issues that are discovered, businesses can greatly reduce the risk of cyberattacks.Secure Configuration:
Another essential aspect of Cyber Essentials is ensuring secure configuration of systems and devices. This involves implementing industry best practices for configuring hardware, software, and network components to minimize potential security risks. By following recommended security guidelines and keeping systems up to date, organizations can significantly enhance their overall security posture.Access Control:
Maintaining strict access control is crucial in safeguarding sensitive data and resources. Cyber Essentials emphasizes the importance of implementing strong user authentication mechanisms and restricting access privileges based on the principle of least privilege. By carefully managing user accounts, enforcing strong passwords, and monitoring access logs, organizations can better protect their digital assets from unauthorized access.
Cyber Essentials
Remember, Cyber Essentials serves as a foundational framework for businesses to establish a solid cybersecurity baseline. It helps organizations take vital steps towards strengthening their overall security posture and protecting themselves against common cyber threats. By focusing on these key components, businesses can significantly reduce their vulnerability to cyberattacks and enhance their online security.
Implementing Cyber Essentials
Creating a Secure Network:
When implementing Cyber Essentials, the first step is to ensure the creation of a secure network. This involves setting up firewalls and installing antivirus software to protect your systems from unauthorized access and malicious software. Regularly updating and patching your network infrastructure is also crucial to prevent vulnerabilities that hackers can exploit. By establishing a strong and secure network, you can safeguard your valuable data and provide a safer online environment for your organization.Implementing Strong Access Controls:
To enhance online security, it is vital to implement strong access controls within your organization. This means controlling and monitoring who has access to sensitive information and system privileges. Implementing multifactor authentication (MFA) can significantly strengthen access controls by requiring users to provide additional verification beyond their passwords. By properly managing user accounts, limiting access to necessary information only, and regularly reviewing access permissions, you can reduce the risk of unauthorized access and potential data breaches.Educating Staff on Cybersecurity Awareness:
The final step in implementing Cyber Essentials is to educate your staff on cybersecurity awareness. Employees play a crucial role in maintaining online security, and their actions can directly impact the overall safety of your organization. Conduct regular training sessions to educate staff members about potential cyber threats, phishing attacks, and best practices for handling sensitive data. Encourage a culture of security awareness, where employees are vigilant about identifying suspicious emails or websites. By empowering your staff with the necessary knowledge and skills, you can build a stronger defense against cyber threats.
Remember, implementing Cyber Essentials is an ongoing process that requires regular monitoring, updating, and adapting to evolving cyber threats. By following these essential steps and continuously prioritizing online security, you can significantly reduce the risk of cyberattacks and keep your organization safe.

